INTRODUCTION
Eternal Blue, an exploit allegedly discovered by NSA’s (National Security Agency) Equation Group and later leaked by the group shadow brokers (allegedly from Russia) (Wikipedia, 2022). This exploit dates back to the early nineties with the introduction of the SMB (Server Message Block) utilized for communication between client and server and created by Barry Feigenbam for IBM in 1983 (Wikipedia, 2022). Eternal Blue was famously used in the ransomware WannaCry that has taken hostage the UK national health system in may 2017 (Wikipedia, 2022).

HOW DOES IT WORK?
Eternal Blue sounds like an interesting exploit with a captivating name, but how does it work? To make is simple, Eternal Blue exploits a vulnerability present in SMBv1 servers called CVE-2017-0144 (mitre.org). By sending especially crafted packets it is possible to cause a buffer overflow that ends up in the file srv.sys making it possible to execute arbitrary code (Checkpoint, 2017). Once this possibility opens up, NSA developed a second exploit called DoublePulsar that act as a back door and can be planted on the hacked machine to allow for shell code execution. (Securityweek, 2017).
WHERE WAS IT USED?
This specific exploit was incorporated in the famous ransomware WannaCry. After Eternal Blue was executed and Double Pulsar planted, the ransomware would than be uploaded to all infected machine and encrypt all files.
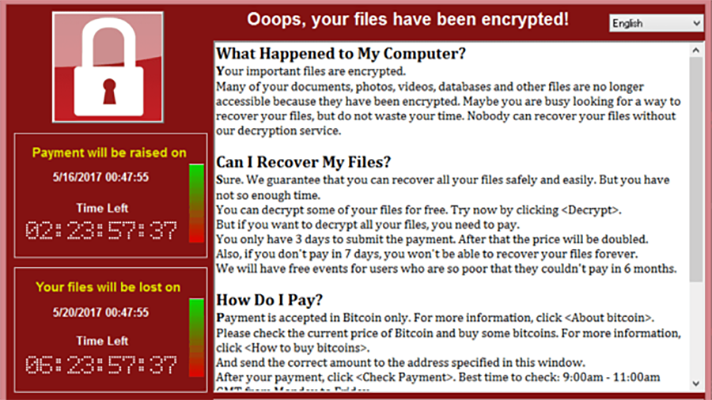
CONCLUSION AND RECOMMENDATIONS
So now that we have learned about this dangerous exploit, how can we stay safe from it? By far the most important thing to do is to make sure that you have applied the security patch MS17-20. Generally remember that opening unknown files and clicking on unknown link in the web could lead to potentially dangerous consequences like getting infected with WannaCry.
References
Argire, I. (2017). Hackers are using NSA’s DoublePulsar Backdoor in Attacks. https://www.securityweek.com/hackers-are-using-nsas-doublepulsar-backdoor-attacks
Grossman, N.(2017). EternalBlue – Everything There Is To Know. https://research.checkpoint.com/2017/eternalblue-everything-know/
Mitre. https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0144
Server Message block (2022). Wikipedia. https://en.wikipedia.org/wiki/Server_Message_Block
The Shadow Brokers (2022). Wikipedia. https://en.wikipedia.org/wiki/The_Shadow_Brokers
WannaCry Ransomware Attack (2022). Wikipedia. https://en.wikipedia.org/wiki/WannaCry_ransomware_attack







